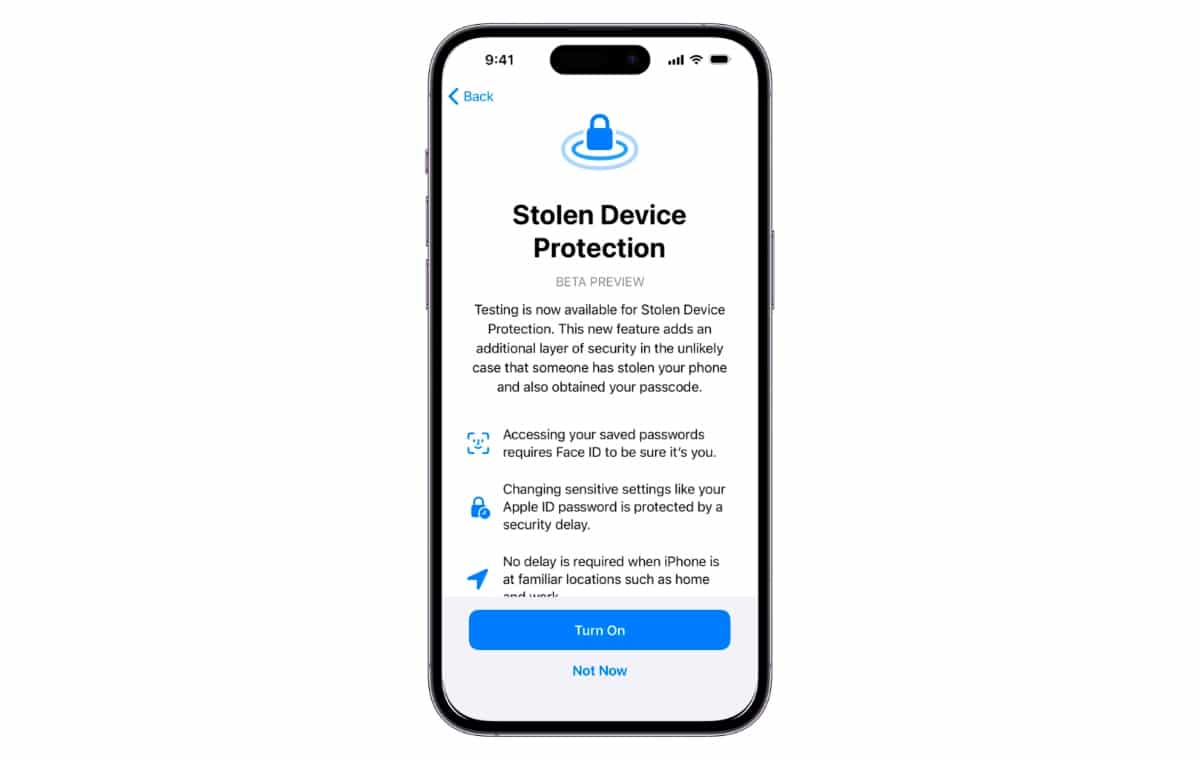
Taken Gadget Security is an element Apple expects will forestall the complete loss of an Apple ID if an iPhone and password are taken. This is the way to get it set up.
Beforehand, a criminal could gain proficiency with an individual’s password through friendly designing or spying, take the individual’s iPhone, and immediately keep the individual out of their Apple ID. After reports of such issues got out, Apple dealt with an element to assist with moderating the gamble of complete misfortune after an iPhone was taken.
As of iOS 17.3, Apple has furnished clients with a method for moderating the danger of all out loss of an Apple ID. A criminal can never again get to basic data or change passwords without biometric validation by empowering Taken Gadget Security.
How to enable Stolen Device Protection
There are some caveats to Stolen Device Protection, but we’ll get into that in a moment. For now, here’s how to enable the feature.
- Open the Settings app and tap on “Face ID & Passcode”
- The toggle for Stolen Device Protection is about midway down the page
- Toggle the feature on and read through Apple’s prompts about the feature
That’s it — Stolen Device Protection is on. However, what that toggle changed across iOS is much more complicated.
From our use of the feature, users shouldn’t notice any difference in how their iPhone operates day to day. This is especially true when in significant locations like work or home where the feature isn’t active.
What Stolen Device Protection does
Taken Gadget Insurance eliminates password backup while getting to basic segments of Apple ID or gadget settings. It likewise executes a security delay when a client endeavors to change particularly delicate data like an Apple ID secret word.
Typically, certain activities will provoke the client for Face ID or Contact ID. In the event that those biometrics neglect to validate, the client is provoked for a password.
At the point when Taken Gadget Insurance is empowered, the accompanying requires biometric confirmation with no password contingency plan:
- Using passwords or passkeys saved in Apple Passwords
- Applying for a new Apple Card
- Viewing the Apple Card virtual card
- Turning off Lost Mode
- Erasing all content and settings
- Take certain Apple Cash and Savings actions in Wallet
- Using payment methods saved in Safari
- Using your iPhone to set up a new device
That implies a hoodlum with your iPhone and password couldn’t get to these settings. Any of these settings could prompt critical monetary misfortune or split the difference of the client’s Apple ID.
Highlights not referenced in the above rundown will in any case have a password backup choice, such as confirming Apple Pay. In any case, FDIC protection will cover deceitful charges in the event that a hoodlum utilizes Apple Pay.
Apple adds one more layer of security for particularly delicate settings and controls — a one-hour delay. On the off chance that the client is beyond a confided in area and endeavors to modify the accompanying settings, a biometric examination followed by an hour delay and another biometric filter happens.
- Changing your Apple ID password
- Updating Apple ID account security settings, like removing a trusted device, trusted phone number, Recovery Key, or Recovery Contact
- Changing your iPhone passcode
- Adding or removing Face ID or Touch ID
- Turning off Find My
- Turning off Stolen Device Protection
Believed areas are advanced by the iPhone and are not client addressable. Critical areas like home and work are utilized as exceptions for Taken Gadget Insurance.